A lot has happened in the last few days since the 19th February 2024, in the dark world of Ransomware gang activity. LockBit ransomware operations have been disrupted by a coordinated effort led by global law enforcement agencies in ‘Operation Cronos.’ Learn more about this significant development and how it impacts cybersecurity worldwide.
Introduction: LockBit, a notorious ransomware gang, has faced a major setback as law enforcement agencies execute ‘Operation Cronos’ to seize several of its operations. In addition, two LockBit actors have been arrested in Poland and Ukraine at the request of the French judicial authorities. Three international arrest warrants and five indictments have also been issued by the French and US judicial authorities. Here’s what you need to know about this crucial development.
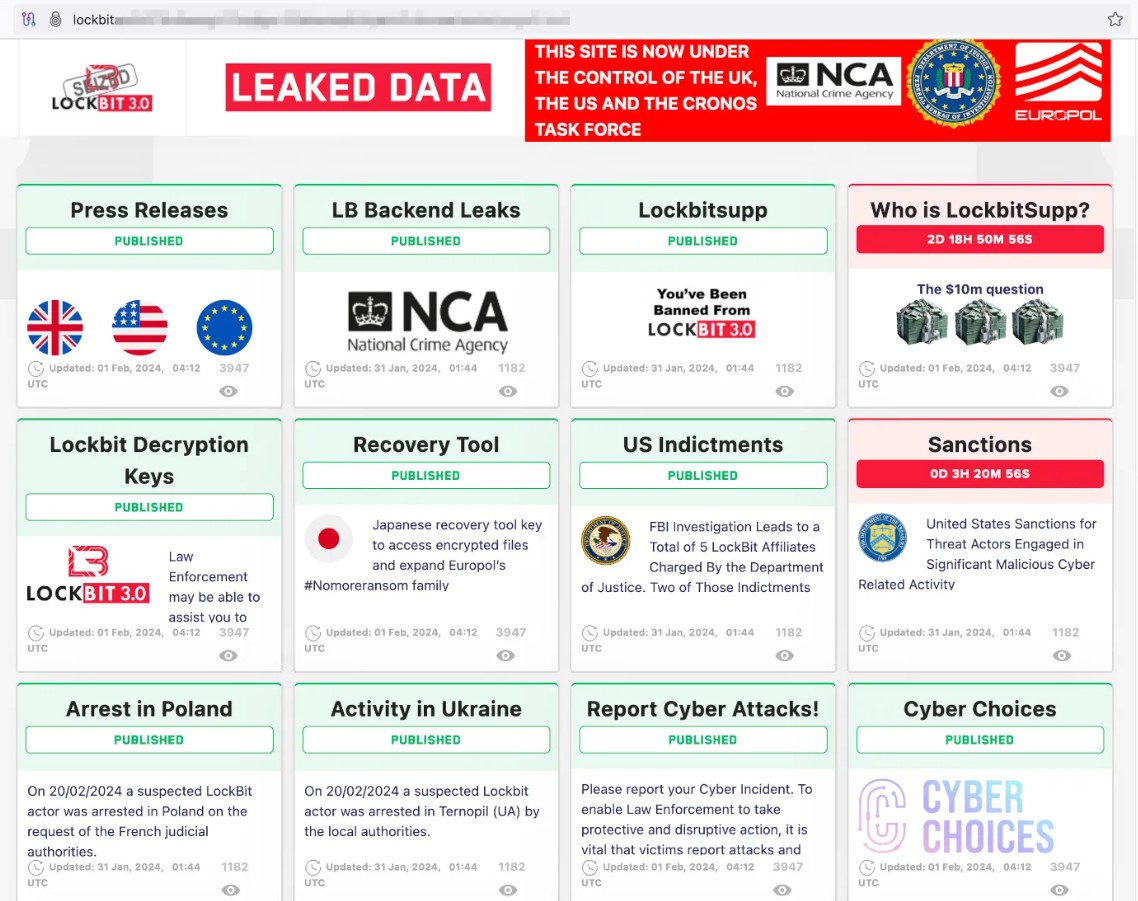
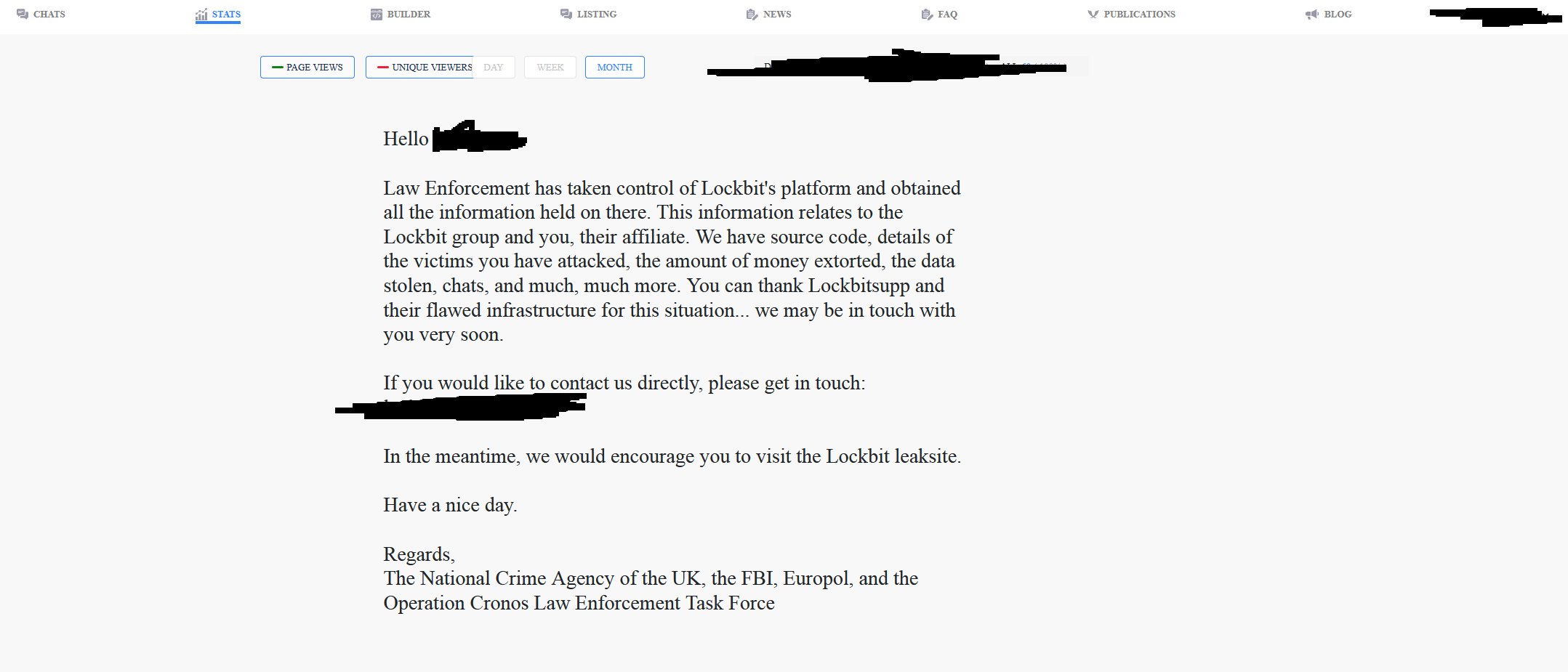
LockBit Websites Seized: LockBit websites now display a takeover message by authorities, indicating a full disclosure of operations. Global law enforcement agencies have taken control of eight “.onion” domains owned by the ransomware group, with messages confirming their control over the sites.
Home Secretary James Cleverly said:
“The National Crime Agency’s world leading expertise has delivered a major blow to the people behind the most prolific ransomware strain in the world.
“The criminals running LockBit are sophisticated and highly organised, but they have not been able to escape the arm of UK law enforcement and our international partners.
“The UK has severely disrupted their sinister ambitions and we will continue going after criminal groups who target our businesses and institutions.”
Further Details Expected: Now there has been official confirmation and press release regarding the seizure, https://www.nationalcrimeagency.gov.uk/news/nca-leads-international-investigation-targeting-worlds-most-harmful-ransomware-group and the displayed messages on the Lockbit Blog suggest that even more information about ‘Operation Cronos’ will be revealed soon by the NCA (National Crime Agency), FBI (Federal Bureau of Investigations) and other law enforcement agencies. This makes it one of history’s most significant law enforcement operations against cybercrime.
Impact on LockBit’s Operations: The takedown has not only seized key operations of the ransomware gang but has also locked out LockBit’s affiliates attempting to access the affiliate panel. This panel serves as a central control hub for managing various LockBit ransomware activities.
LockBit’s Rise and Fall: LockBit ransomware-as-a-service (RaaS) gained rapid prominence since its inception in 2019, quickly becoming one of the most widely used ransomware strains by 2022. However, with the recent takedown operation, its reign faces a significant challenge.
Implications for Cybersecurity: This seizure marks a crucial victory in the fight against ransomware. Organizations worldwide should take proactive measures to safeguard their systems and data against such threats. Stay informed and implement robust cybersecurity practices to mitigate risks.
Conclusion: The seizure of LockBit ransomware operations underscores the importance of collaboration between law enforcement agencies and cybersecurity experts. Not just in the UK, but America, Europe, Hong Kong and Asia in a worldwide effort to thwart this threat. Thousands of criminal hackers will now be worried and seeking shelter, from the net of law enforcement that will be closing in. The new few months will be uncertain, but many of the criminals will regroup and adapt to continue extorting money from victims. Currently the stakes are too high, and unethical hackers can make a lot of money, (if not become rich) from ransomware attacks, so why would they stop if they don’t think they have been caught. For companies and organisations trying to avoid being targeted, Brainstorm Security Ltd strongly suggest staying vigilant and implementing robust security measures, 2FA, encryption of data while in transit and at rest, having backups and testing them. We also suggest planning for when you get breached, by having systems practiced during tabletop exercises, incident response (IR) teams, negotiators already in place to support your organisation, so it can defend against ransomware attacks and protect it’s valuable data.
